Home » Research » About » IT vs OT | When Facing The Insider Threat | What Happend | Free Software vs Open Source | ask me |
CONVERSATION: Cueball and Priscilla are on a first date and Cueball is trying to strike up a conversation by asking Priscilla what she does in her free time. ★ Priscilla has probably been dreading this question, because she answers that her free time activity consists of trying to figure out how to respond if asked what she does in her free time. Cueball answers soothingly, but Priscilla anxiety gets the better off her and she leaves abruptly.
During Priscilla speaking, Cueball finished all of his drink. He may have been surprised by the reply, and Priscilla sensing this contributes to her leaving.
The title text implies that she also spends her free time wondering what to write in her diary (with no success).
Both the comic and the title text are examples of self-referential humor. Priscilla recognizes that she spends her free time thinking what to say about her free time, so she must spend some of that free time thinking about her thinking about her free time. Such self-referential loops are often disturbing, since they contain within them potential for infinite regression. On the other hand, there is a simple way to exit the loop before any recursion. Priscilla has already decided what to say when asked what she does in her free time, and she has figured out what to write in her diary. But on realizing this, Priscilla would have to find something else to occupy her free time, such as going on a date.
Insider threat tactics: The hacker speaks by Priscilla
· Priscilla Felicia Harmanus · 1993 from the Netherlands · Last update: 21 aug 2020
How I discovered Free Software and met RMS ★
How To Install Proprietary Closed Software In Ubuntu ★
Your Grandma on linux - explain
No one knows who I am yet and what kind
of content I produce. So why not focus on a topic that
people are already searching for, right?
Second, there is the question of skill or interest. ★ Many people who want to write books, teach courses and/or build websites do not have either the skill or the interest to perform all of these customization steps. And spent years teaching courses in computer programming and website construction. It is understandable that many people do not even know how to right click on their computer screen - much less copy and paste cryptic commands into the Linux “black box” terminal. In order to solve this problem of helping folks have a customized operating system, without making all the customizations themselves, DistroTweak created a new and revolutionary way to quickly and easily share our custom operating system. For this new way it is called a “DistroTweak” and their describing it here for the very first time.
What are Socio-Technical Systems? ★
A socio-technical system (STS) is one that considers requirements spanning hardware, software, personal, and community aspects. It applies an understanding of the social structures, roles and rights (the social sciences) to inform the design of systems that involve communities of people and technology. Examples of STSs include emails, blogs, and social media sites such as Facebook and Twitter.
The basis of STSs is general systems theory, which describes what the disciplines of science have in common—i.e., that they all refer to systems: sociologists see social systems, psychologists cognitive systems, computer scientists information systems, and engineers hardware systems. In general systems theory, no discipline has a monopoly on science—all are valid.
These disciplinary perspectives on computing allow us to view computing through distinct levels and trace its evolution. Computing began at the mechanical level (hardware devices), evolved an information level (devices + software), then acquired a human level (IT + human-computer interaction), and finally a community level (STSs). A community works through people using technology, as people work through software using hardware. Consequently, social requirements are now an important part of computing design.
While sociologists study the social level alone as if it were apart from physicality, and technologists study technology as if it were not part of society, socio-technology is a distinct field of inquiry on how personal and social requirements can be met by IT system design. As such, STSs seek to merge people and technology, viewing the integration of computers into societal systems as the next evolutionary step of humanity. An STS approach to design raises the cost of development but results in complex systems, like social networks, that have far more performance potential. Exploring a design problem by rising to an STS mindset can reveal further dimensions of a design’s use potential and inspire development.
Home » Research » About » IT vs OT | When Facing The Insider Threat | What Happend | Free Software vs Open Source | ask me |
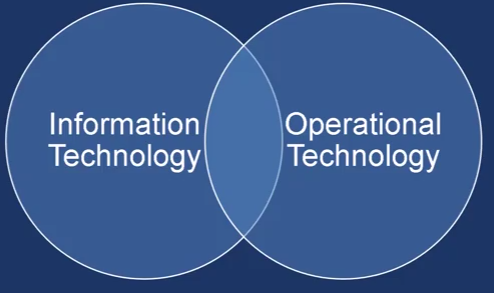
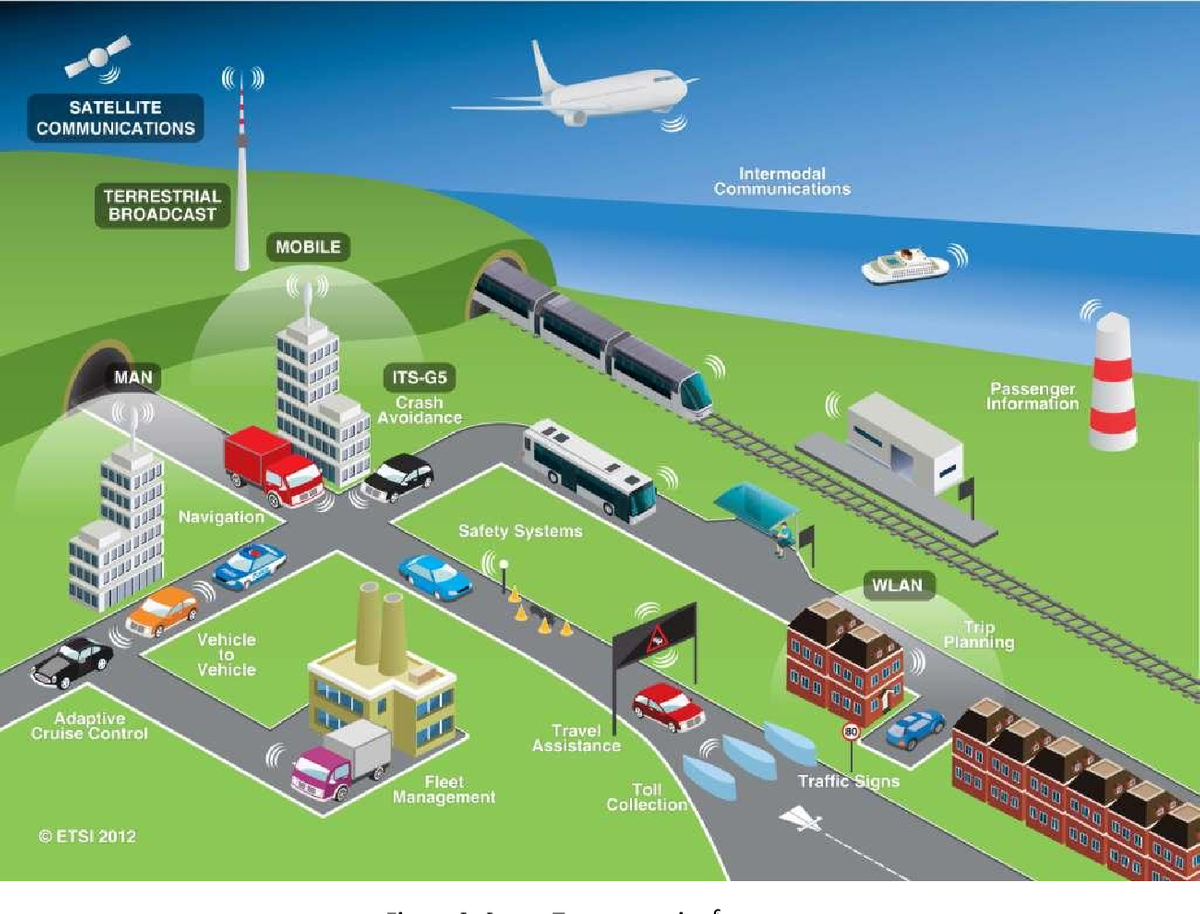
Cybersecurity voor Industrial Automation
where the physical and digital world come together
This is a new web page...
Home » Research » About » IT vs OT | When Facing The Insider Threat | What Happend | Free Software vs Open Source | ask me |




%20M2M%20connected%20devices.jpg/picture-1200?_=17133ac38e8)





